Our research into Ethereum transaction security began with an analysis of real-life instances of spam, exploits, and other malicious activities. By examining these cases, we identified distinct behavior patterns associated with both attacker and victim addresses. These patterns often reveal critical insights into the tactics and strategies used by malicious actors, as well as the vulnerabilities exploited.
Let’s delve into some of the more intriguing properties of these addresses, highlighting key factors that can indicate potential security threats.
Which address data can uncover security concerns?
Several types of address data can indicate potential security threats or malicious activity. Here’s how to analyze the addresses and what to look out for.
1. Address/token similarity
Address similarity measures the resemblance between a given address and well-known, reputable addresses by analyzing the edit distances of their prefixes or suffixes. This technique helps identify potential phishing attempts, where attackers craft addresses that closely mimic legitimate ones to deceive users.
Since most platforms only display the first and last few characters of an address, users can inadvertently select the wrong one to transact with, falling victim to these attacks. By comparing these segments, we can detect subtle differences and warn users of potential threats.
On the same note, token symbol similarity assesses the resemblance between the token symbol in question and those of well-known tokens by analyzing their edit distances. This method can reveal phishing schemes where attackers create token symbols that closely resemble established ones, intending to mislead users. A symbol that imitates a recognized token may trick users into transacting with a fraudulent token instead of the genuine one. By evaluating these similarities, you can flag suspicious tokens and protect users from deceptive practices.
2. Token value trend
Monitoring the fluctuations in the USD value of a token is crucial for detecting potential rug pull scenarios, whether intentional or accidental. By tracking these changes, one can identify sudden or unusual drops in token value, which may signal malicious activities such as market manipulation or exit scams.
Rug pulls typically occur when developers or significant holders suddenly sell off their positions, leaving other investors with worthless tokens. Additionally, observing value trends can provide insights into the overall health and stability of a token, helping users make informed decisions. This proactive approach serves as an early warning system, alerting users to potential risks and protecting them from financial losses.
3. Historical gas usage
As the amount of gas used depends on the complexity of the operation, tracking historical gas usage is essential for identifying unusual patterns in Ethereum transactions. For each user, you can monitor the gas usage statistics of transactions initiated by their wallet. This data is crucial for detecting anomalies, such as unexpectedly high gas consumption.
For instance, if a wallet exhibits gas usage significantly above its normal pattern, it can indicate unusual activity, prompting a warning. This could suggest a user is engaging in a particularly complex transaction, potentially involving new or risky behavior.
Additionally, you can track gas usage statistics for each contract's function calls. By analyzing the gas consumed in these calls, you can detect when a function is using more gas than usual. A sudden increase in gas usage may signal that a function call is executing differently from previous instances, which can be an indicator of a change in the contract's behavior or a potential hack.
This kind of monitoring helps identify whether a contract has been compromised or if there's a significant shift in how it's being used. By maintaining a detailed record of gas usage, you can provide early warnings and safeguard against potential threats.
4. Recent contacts
Monitoring recent contacts with Ethereum addresses is key to maintaining transaction security. The basic principle is straightforward: whenever you're about to interact with an address for the first time, this event should be flagged as it represents a potential security risk.
However, over time, the list of contacts can become unwieldy, so it's crucial to prioritize and remember only several more significant entries. Determining what constitutes a "contact" is also essential as it can include transaction calls, fund transfers, or approvals.
Additionally, each type and direction of a contact carries different implications and potential risks, so it’s important to keep track of the nature of past interactions with an address. For instance, if an address has previously only received funds from another address but is now about to send funds, this shift in behavior might warrant a warning.
Similarly, if an address is about to grant an approval for a fund withdrawal or transfer to an address for the first time, this action should also be flagged. Such changes can indicate a significant alteration in the address's behavior or purpose, potentially signaling a compromised account or a phishing intent.
5. Function-to-event correlation
Capturing actions like transfers, approvals, or ownership changes, events in smart contracts are crucial for monitoring and auditing blockchain transactions.
The function-to-event correlation technique provides a nuanced approach to understanding the specific actions performed by a smart contract function. This method involves programmatically analyzing the execution flow of a function, where all events logged during its execution are identified and recorded. The key assumption here is that the significance of each well-known event is predetermined; here think transfers, approvals, burns, mints, ownership transfers, etc.
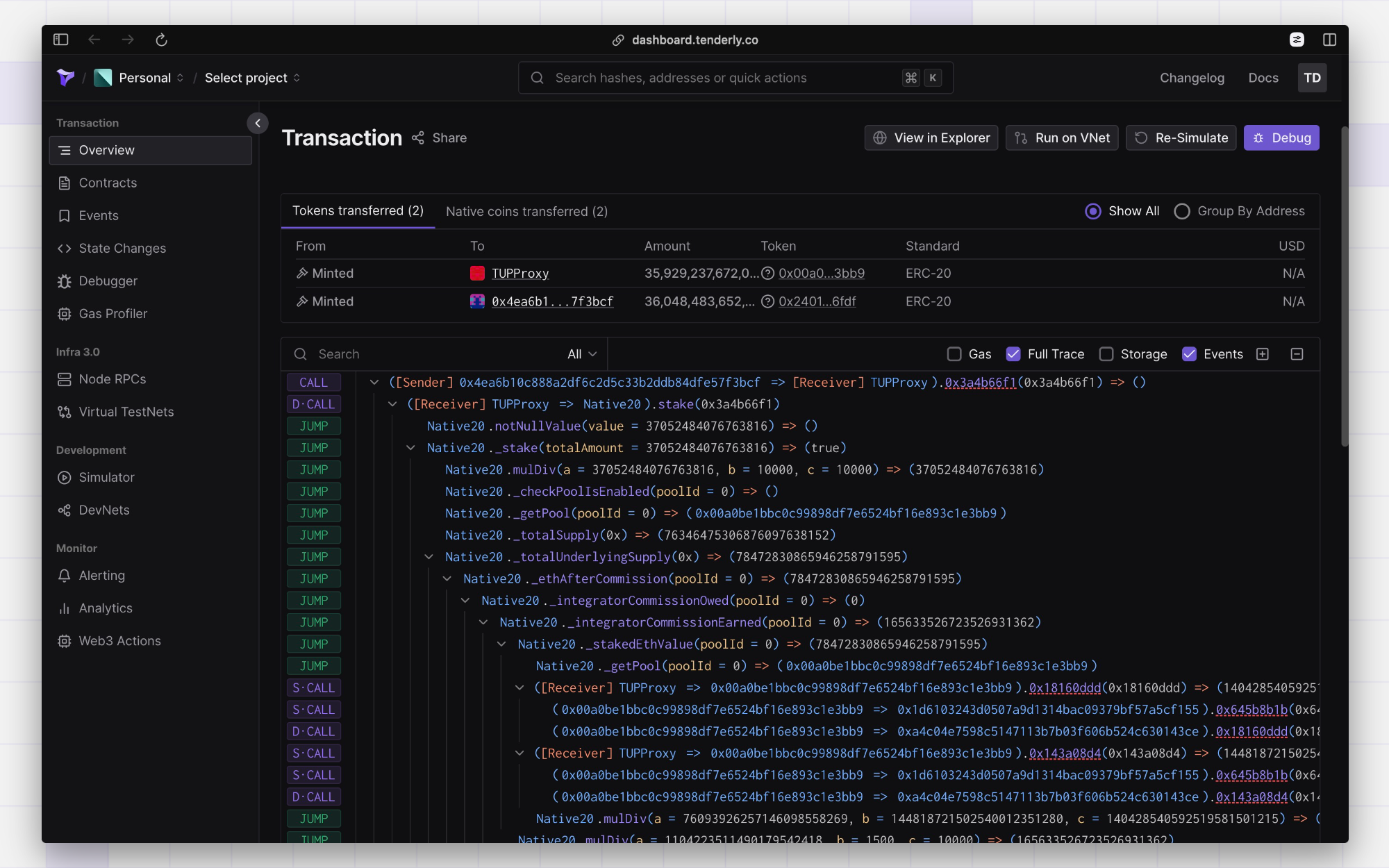
By associating these log events with the functions they occur within, you gain valuable insights into the expected outcomes of a function call. This correlation helps in building a behavioral profile of the function, indicating what actions are supposed to happen under normal circumstances. For example, if a function is typically associated with a transfer event, and that event does not occur during a specific execution, it raises a red flag.
Such discrepancies can indicate potential issues, ranging from benign changes in contract logic to more serious concerns like function misbehavior or even malicious tampering. Detecting when expected events are absent during a function's execution is a critical part of maintaining contract security. It serves as an early warning system, prompting further investigation to ensure the contract operates as intended and has not been compromised.
How to handle large-scale blockchain data
The listed address details are relatively simple data structures, but the entire processing pipeline required for this type of analysis is a significantly more complex challenge.
Consider the task of analyzing the entire Ethereum mainnet, which consists of over 2 billion transactions spanning more than nine years of real-time data. The goal is to process all this data within a seven-day timeframe, necessitating the design of an intricate and efficient pipeline.
Fetching transaction traces
The first step involves retrieving traces of all transactions, which record all internal operations executed during each transaction, such as function calls and logged events. These records are initially fetched in a raw format, but we subsequently decorate them with additional context and metadata to provide more detailed insights.
Traces must be fetched in large batches, far exceeding real-time speeds, which requires massive parallel data transfer capabilities. Given the volume of information, the process cannot rely on sequential operations alone.
We must analyze batches of transactions in chronological order to maintain temporal accuracy while also leveraging parallel processing to handle the sheer volume of data. This dual requirement ensures that we can process incoming data without bottlenecks, enabling us to keep pace with the blockchain's scale.
Efficient data storage
Once the data is processed, it needs to be stored efficiently. Persisting data after each processing step would be inefficient due to the significant time it would take for database read/write operations.
Instead, we determined optimal intervals and data chunk sizes for pushing data to the database, balancing the need for timely data storage with system performance considerations. This careful timing ensures that data is stored without overwhelming the database, maintaining system stability and efficiency.
Laying the groundwork
Handling such a vast amount of blockchain data requires a sophisticated pipeline that combines rapid data retrieval, parallel processing, and strategic data persistence. This approach not only enables the timely analysis of the Ethereum blockchain but also lays the groundwork for scalable solutions capable of handling future increases in data volume.